Attack Pattern Enumeration - Social Engineering

Attack Pattern Enumeration - Social Engineering

Common Attack Patterns in Social Engineering
Organizations across the continents have made an umpteenth number of news stories in the past few decades wherein they have been attacked by either ransomware or found a software vulnerability that paved an easy entry for the attackers. The adversaries win 89% of the time, and this number keeps soaring every year. We all know such attackers and attacks and organizations are buckling up themselves by investing in advanced technologies to shun these types of attacks. However, enterprises tend to forget that amidst procuring fancy technologies to safeguard their businesses, the biggest threat within their organization is still open and vulnerable. This threat is called “human psychology.” The attackers who target human psychology are called “social engineers.”
Social engineer types of attackers use their social engineering techniques, i.e., the art of manipulating the workforce to unintentionally release private and confidential information. Cybercriminals use social engineering tactics by using various techniques to fool the target individuals to gain human trust and learn a few confidential information about them. This information can be anything based on the attacker’s motivation, such as if the attacker’s motivation is to gain financial benefit out of this attack, they may fool wealthy individuals to let out their banking passwords. However, just a Lion closely monitors its prey before attacking; similarly, the adversary will closely monitor its target individual, learn all monetary channels, and target only a few beneficial ones. For instance, a significant cryptocurrency trading firm recently conducted a general survey of individuals entering the crypto market base in 2021, and it was found that a staggering 60% of business owners joined the market in just 2021. Are you thinking what I’m thinking? Yes, the wealthy target individual also seriously diversifies his wealth in the crypto market base. Well, the adversary has enough motivation by now!
This was just a glimpse of a plausible attack vector that can happen on most SMBs and startups that do not have enough security measures in place but do hold tons of private and confidential information. Wouldn’t you want to know at least a few common attack patterns that these social engineers follow and succeed most of the time? Read on to know these common attack patterns.
Identity Spoofing
Identity spoofing is an attack pattern wherein the cybercriminal imposes somebody’s identity and then uses that identity to commit fraudulent, criminal motivation. This type of attack is the most prevalent one used by amateur attackers who dream of becoming experienced and sophisticated attackers. It’s funny how attackers have such aspirations too. Nonetheless, identity spoofing is a cyber criminal’s first chapter in their cybercriminal handbook. However, this little handbook of theirs includes many attack patterns that follow identity spoofing as their base attack pattern but changes their traits down the line in the attack chain. Let’s discuss a few of these attack patterns with a common goal to pilfer money, gain human trust in return for confidential data.
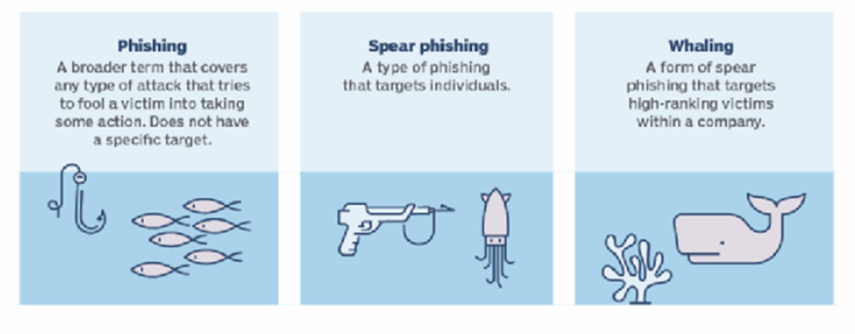
Phishing and Spear Phishing: Email is indeed considered a boon to humanity. Let me rephrase the previous statement. Email is indeed considered a boon to humankind until you’re phished! Phishing is a term allotted to an event when an attacker sends you a malicious email with links and attachments only to gain privileged access to your email or email servers unbeknownst to you. The email usually looks legitimate, often purporting to be from a third-party vendor or a trusted source to an individual or a company. A phishing attack ideally targets a more vast audience simply because the attacker doesn’t know anybody from the target organization that holds a tendency to trust emails from unknown sources in a jiffy, but they do know somebody will trust them for sure.
However, as every attack has an elevated attack, so does phishing. It is called “spear-phishing.” Spear phishing is a targeted attack on a specific individual who might have elevated access within the organization whose identity could be used to gain financial information. The buck doesn’t stop here. There’s yet another level of spear-phishing, which is commonly known as “whaling.” Whaling is a type of attack wherein an attacker targets someone very senior within an organization whose identity, when impersonated, can make a world’s difference to the attacker and the organization itself. According to a recent survey led by a leading firm in email security, some interesting figures such as approximately 88% of SMBs and startups fall prey to a phishing attack in just about the last six months. That’s a lot in the social engineering bucket.
Manipulate Human Behavior
Have you ever wondered why most of the real estate agents in the Americas are women? Have you ever wondered why every Bond movie has a pretty-looking actress alongside Bond himself? Well, let me explain to you this analogy. Most real estate agents who are women tend to get along well with the buyer to know the buyer’s credibility in the very first meeting. This helps the agents to save time by knowing who can afford it and who is just browsing. This human psychology adapted by feminine agents does wonders for them in understanding their buyer in no time.
On the other hand, we all know James Bond is a detective in all its movies. However, little do we know that a beautiful woman is aligned with the role to honey trap or impersonate as someone trusted for the villain in every film. This active role of manipulating the villain’s human psychology always works for Mr. Bond.
This is precisely what an adversary does in this type of attack pattern. The attacker exploits the target’s human psychological behavior by impersonating a trusted individual appointed for the same job the target wants to accomplish. However, little does the target know that the adversary is there to influence a trusted identity to embezzle confidential information or achieve his goal. This phenomenon can also be termed “Pretexting.” There are various ways to execute pretexting, such as Pretexting via Customer Service, Pretexting via Tech Support, Pretexting via Phone, and many such social engineering techniques.

Detection and Mitigation
Organizations and businesses must comprehend that their network infrastructure is only as strong as their weakest link, and humans cannot be their weakest link. Therefore, educating the workforce about such attack patterns and implementing an innovative program is the topmost security measure an organization can plan. Considering a human-centric focal point, there are a few steps that every firm can design and implement in any environment.
Here are a few practical steps organizations can incorporate into their security programs:
- Train and educate the workforce to keep them apprised of emerging social engineering attacks.
- Implement email security measures.
- Invest in robust anti-virus software and configure it in a way that suits your organization's nature of business.
- Avail bird's eye view of your infrastructure with complete visibility of every person's activity.
- Maintain a track record of what data is accessed by whom.
- Include surprise phishing simulators to prepare and know vulnerable individuals in an actual attack.
- Implement industry best practices such as NIST, CIS over and above regulatory and compliance frameworks.
Conclusion
Unfortunately, some companies ignore the social engineering aspect of an attack and focus more on sophisticated attacks like the ransomware and top 10 OWASP vulnerabilities but little do they know that preventing a social engineering type of an attack is cyber security 101. This norm will only make one’s enterprise look weak even though it may earn millions from their businesses. However, the fact is, preventing social engineering attacks is much easier than stopping a sophisticated attack. It is essential to understand the human psychology within every company to begin educating the workforce and then setting up security measures above that.