Latest in Detection and Response - XDR

Latest in Detection and Response - XDR

XDR for a Realtime Cohesive Threat Response
The longer an attacker can exist undetected on a network, the more time they can cause damage. According to a FireEye M-Trends report, the average dwell time in 2021 was 24 days, down from 56 days in 2020 [1]. As a result, corporate Information Security teams look to threat detection and response technologies to decrease dwell time. But which ones are most effective at reducing the dwell time of malware on systems?
The terms Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), Endpoint Protection (EPP), and Endpoint Detection and Response (EDR) have all enjoyed their day in the sun. Still, Extended Detection and Response - XDR is the buzzword to become familiar with. XDR correlates and analyzes information from all points in the network, providing a cohesive, Machine Learning (ML) enabled threat response. XDR technology aims to detect unknown threats to prevent them and maintains continuous monitoring and system sanity checks. While the number of attacks rises yearly, real-time cohesive threat detection and response orchestration, namely XDR, decreases attack dwell time.
The Ever-Growing Complexity of Networks
It has been over a decade since Cloud technology flooded the IT industry, expanding corporate networks beyond the traditional LAN and WAN concepts to a Cloud-driven one. Resources found a new home outside private network architecture in large shared data centers. Cloud has allowed companies to share economies of scale and benefit from network effects. Still, it also increased the complexity of security orchestration due to the architectural diversity of cloud platforms. IoT devices have recently grown in popularity, and the pandemic response has moved many employees to a work-from-home model.
All these factors have ballooned the corporate attack surface. In 2021, the impact of this ballooned attack surface was apparent. Cyber attacks are more numerous and more costly. Companies have had to respond with increasingly complex IT security measures.
Detection and Response Tools Needed To Evolve
IDS and IPS attempt to detect (IDS) or prevent (IPS) cyber-attacks. They may be installed directly on a host or as a network appliance. When access control rules are violated, network anomalies are detected, or known malware signatures are found, IDS alerts a Security Operations Center (SOC). At the same time, IPS takes additional automated actions to prevent malicious activity [2].
One problem with signature-based detection is that a traditional Virus Scanner detects only 50-60% of malware, and 90% of samples used in the wild against companies were customized malware [3]. Therefore, post-exploitation efforts are critical to ensure network security since signatures alone are largely ineffective against the APT large companies face.
EDR is IPS on steroids. Continuously monitoring for Indicators of Compromise (IOC), EDR remains vigilant after malware bypasses detection and executes its payload. EDR systems aggregate and correlate forensic and telemetry data at critical waypoints as files enter the endpoint and are acted upon by applications or executed. Suspected IOCs are investigated using advanced ML and assigned a severity score before escalating to the SOC team. This represents a proactive approach to continuous monitoring of endpoint sanity.
A reactive approach is insufficient, and a sustained proactive approach is needed to supplement access control rules and signature scanning. The combined application of ML and Threat Intelligence to monitor post-exploitation IOCs sets EDR apart from other detection and prevention technologies.
XDR Provides A Cohesive Realtime Response
XDR extends EDR, taking the next level to the next level with protection that spans the whole corporate network, aggregating and correlating telemetry data between cloud, appliance, peripherals, IoT devices, and remote workers in real time. When an IOC is detected at any point on the network, forensic and telemetry data is stitched together and analyzed to determine the trajectory and scope of the attack. Both automated responses and detailed SOC team alerts form a cohesive response. ML-enhanced sanity checks can take immediate action on compromised systems via API. At the same time, human SOC team members investigate incident reports of related events at any other potentially affected locations across the whole network infrastructure.
The three main components of XDR are:
- Integration - APIs communicate telemetry data from multiple network entities such as mail servers, web content filter proxies, firewalls, IDS/IPS and UTM appliances, Cloud Access Security Brokers, Access Servers, and EDR.
- Analysis - Data is centralized into a data lake and normalized similarly to SIEM aggregation, allowing correlation of events across the organization.
- Response - The central ML-enabled system can prove nodes for data and conduct system integrity checks, looking for IOC. Immediate action can sometimes be automated, and a SOC can initiate an investigation via remote access and API.
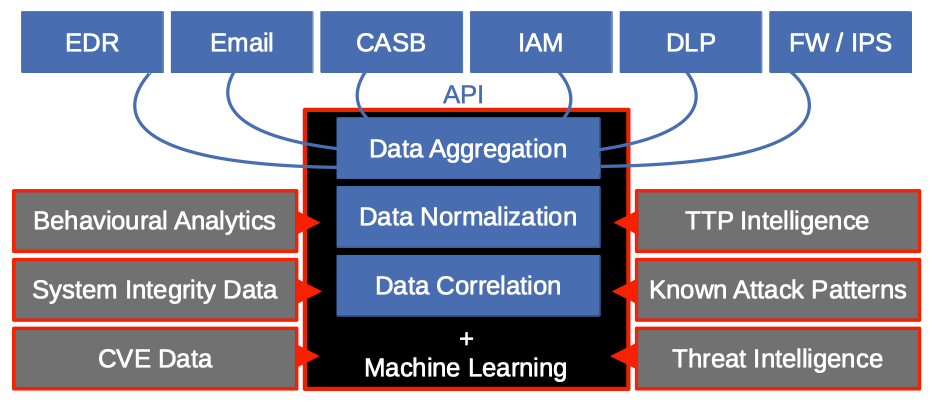
Figure 1 - Extended Detection and Response Architecture - shows the architecture of XDR. All network entities feed telemetry data into an analytics engine. In addition, threat Intelligence and Behavioural Analytics enhance the machine.
Conclusion
Endpoints must be continuously monitored for IOC at the system activity and sanity level because Virus Scanners cannot effectively protect against advanced malware with novel signatures. EDR complements existing Intrusion Detection and Prevention System technology, but XDR provides cohesive threat detection and response across a complex business IT infrastructure. The ultimate goal is to reduce malware dwell time. XDR’s analytic cohesion allows it to trace an attack across the organization and deliver security teams optimal insight for finding and stomping out the intrusion.
References
[1] FireEye - M-trends 2021: Insights into Today’s Top Cyber Trends and Attacks