Leverage MITRE ATT&CK

Leverage MITRE ATT&CK

What is MITRE ATT&CK Framework?
MITRE ATT&CK is a free and open knowledge base of cyberattack tactics and techniques to help cyber security professionals develop analytical insight toward comprehensive cyber threat intelligence (CTI). ATT&CK is an acronym that stands for Adversarial Tactics, Techniques, and Common Knowledge. MITRE ATT&CK’s breadth includes a comprehensive store of all known attack behaviors used by cyber threat actors and is constantly updated with global trend data.
There are 3 main functional matrices in ATT&CK which define the highest-level ATT&CK framework:
- Enterprise ATT&CK - Attack patterns directed at Windows, Mac, Linux, and Cloud Environments, including a pre-attack behavior
- Mobile ATT&CK - Attack patterns directed at iOS and Android devices
- ICS ATT&CK - Attack patterns directed at Industrial Control Systems
ATT&CK Uses TTP As A Primary Perspective
ATT&CK is comprised of 3 main components:
- Tactics - The technical goals of an attack (Initial Access, Establish Persistence, Information Collection)
- Techniques -Each tactic has a list of techniques that define the technical details of an attack (Initial Access techniques include: Spear Phishing, Accessing Valid Accounts, and Leverage a Trusted Relationship)
- Procedures - Attack implementation includes known malware, methods, and names of adversary groups with descriptions and links to external resources. Changing IP addresses, domain names, and minor modifications to malware make attacks challenging to identify and track. MITRE ATT&CK approaches threat intelligence on the Tactics, Techniques, and Procedures (TTP) level, which is much more difficult for adversaries to change (Figure 1). And when they do, MITRE incorporates that new TTP into the ATT&CK framework. Because TPP centered approach focuses on things the adversary cannot change, it guides network defenders toward accurate, reliable solutions.
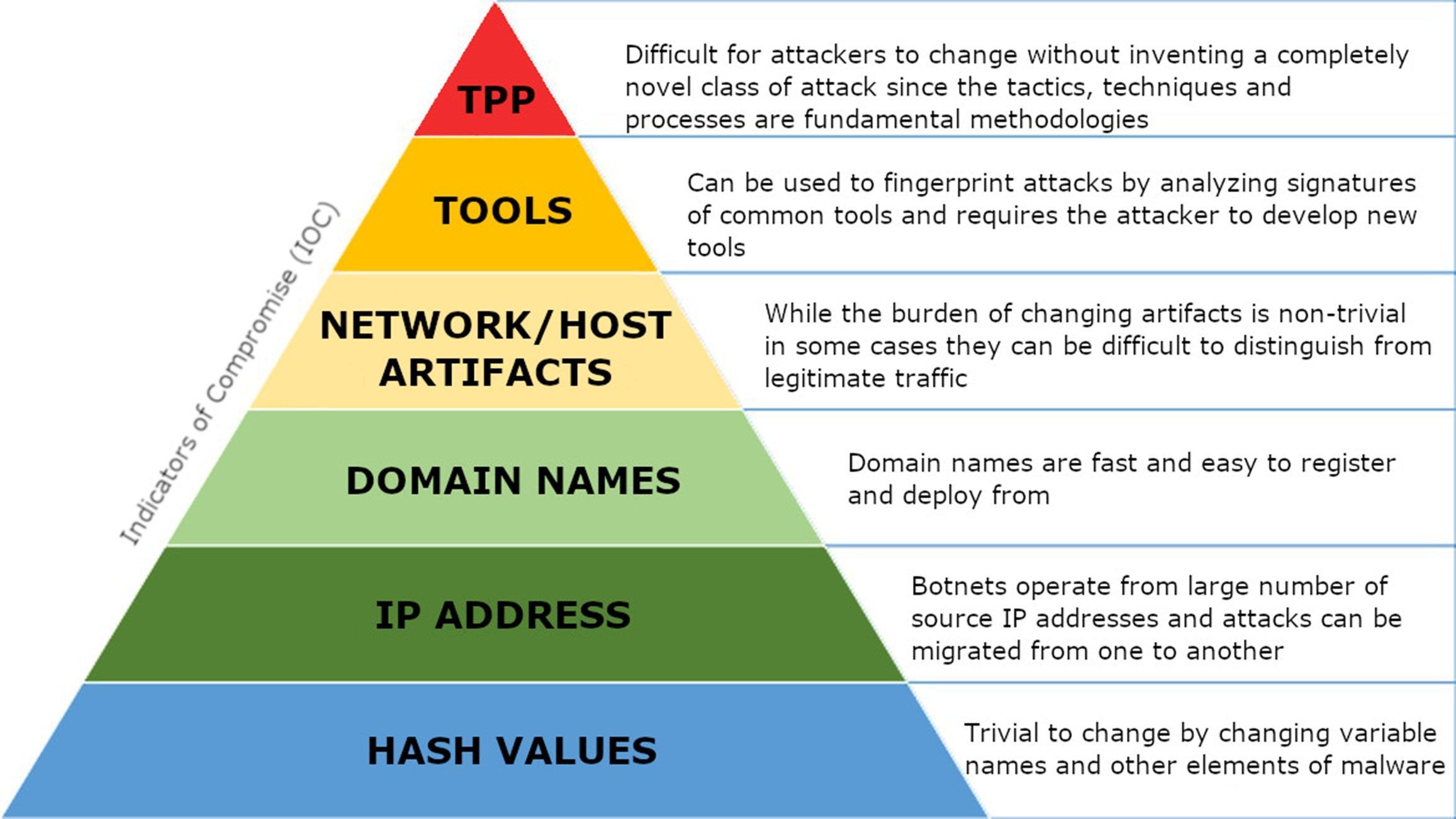
Figure 1. The Pyramid of Pain explains perspectives of attack analysis.
MITRE ATT&CK Use Cases
MITRE ATT&CK spans broad high-level and granular low-level perspectives. For example, by mapping internal threat intelligence to ATT&CK, a security team can generate heat maps for high-level insight to identify where and what kind of attacks are occurring within an organization. At the same time, a granular low-level perspective provides precise technical details that can be used to design and build defenses.
ATT&CK’s threat actor profiles enable more realistic Adversary Emulation for Red Team exercises [1]. In addition, ATT&CK allows an IT security team to test its security implementation against known tactics, techniques, and processes used by Advanced Persistent Threats (APT) in the wild. Also, ATT&CK’s ATP profiles can be used to deploy attractive Honeypots or Honey-nets, aiding early detection.
Implementation
MITRE has maintained a web application called Attack Navigator [2] containing all ATT&CK components in a dashboard-style user interface. The app is a good starting point for understanding adversary behavior and implementing security controls.
The images below (Figure 1 and Figure 2) are taken from Attack Navigator. To understand the scope of ATT&CK a little better, notice that Figure 1 shows a single tactic (Initial Access) with techniques including sub-techniques, while Figure 2 highlights multiple tactics and associated techniques without displaying sub-techniques.
The extent to which MITRE ATT&CK can be used to build analytical metrics depends solely on the size and efforts of an IT security team. For example, a small enterprise can initially focus on the Initial Access tactic to prevent attacks before entering the network. Then, by analyzing Initial Access techniques, a security team can develop a list of Administrative, Physical and Technical Controls for reducing the external attack surface. This can include restricting applications installed on company-owned assets (T1189, shown in red), enforcing strong password complexity and ensuring proper off-boarding procedures for deleting expired user accounts (T1078, shown in green), providing user training on identifying phishing campaigns (T1566, shown in yellow), installing virus detection software (T1189, T1091, T1566, shown in orange), and ensuring all systems receive critical security updates (T1190, T1133, T1195, T1199, shown in purple). These techniques are shown below in Figure 2.
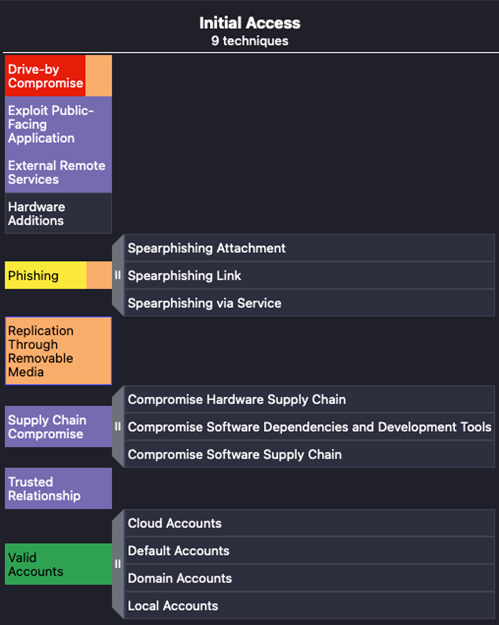
Figure 2. Initial Access Techniques.
A more in-depth examination of ATT&CK post-exploitation techniques for larger enterprises can guide the engineering of hardened cyber defenses. After attackers gain a foothold on a target network, their focus shifts to (but is not limited to) tactics such as Persistence (shown in green), Defence Evasion (shown in orange), Discovery (shown in blue), Credential Access (shown in red), and Lateral Movement (shown in purple). Host, server, and appliance logs can be configured, immediately aggregated, normalized, and searched for indicators of compromise (IOC) (TA0005). Processes on a host can be baselined and monitored to detect both known IOC and anomaly activity that could be caused by novel malware that has evaded virus-scanner detection (TA0002). Finally, NIPS can examine, block, and escalate alerts for any attempts to access non-authorized services (T1021).
Conclusion
MITRE ATT&CK is what the future of cyber intelligence looks like. It is well-structured information that allows comprehensive mapping of the attack surface. It approaches attacker behavior from the TTP perspective, which is difficult for attackers to change. The framework can help track vulnerability management and build detection and response solutions with an initial learning curve. As a result, there is always an opportunity for every team to improve their cyber-defense capability.
References
[1] MITRE - Finding Cyber Threats with ATT&CK-Based Analytics