Security Operations
Build High-Performance Cyber-Resilient Businesses

Security Operations instill Assurance
With its manifold benefits, the digital revolution has brought about an interconnected global ecosystem. With the meteoric rise of the Internet of Things (IoT), cloud computing, and complex enterprise networks, the cyber landscape has grown exponentially, offering a fertile ground for innovation and expanding the attack surface for malicious actors.
Historically, organizations relied heavily on perimeter-based security measures—firewalls, antivirus software, and DMZs—to protect their assets. However, as cyber threats grew in sophistication, this strategy proved insufficient. Cybercriminals armed with sophisticated malware, ransomware, phishing, and social engineering techniques started bypassing these traditional defenses with surprising ease. Furthermore, introducing BYOD (Bring Your Device) policies and a shift towards cloud services introduced new entry points for potential intrusions.
In the rapidly evolving realm of cyberspace, threats proliferating at an alarming rate, necessitating proactive defense mechanisms. fnCyber Security Operations is a linchpin in an organization's digital defense strategy. Tasked with continuous monitoring, detection, and response to security incidents, Security Operations is crucial in safeguarding digital assets, networks, and data from potential breaches and attacks.
fnCyber Security Operations leverages an array of sophisticated tools and practices such as Intrusion Detection and Prevention Systems (IDPS), Security Information and Event Management (SIEM) platforms, and advanced threat intelligence feeds, providing real-time analysis of security alerts generated by multiple systems across an enterprise. With a dedicated focus on network traffic, logs, and patterns, anomalies are swiftly identified, indicating potential breaches or malicious activities.
In addition to detection capabilities, fnCyber Security Operations are equipped to manage and respond to incidents. By coordinating with incident response teams, orchestrating containment strategies, and ensuring effective mitigation of threats, the center ensures minimal disruption and damage to an organization's operations. Employing threat-hunting techniques, the team proactively seeks signs of compromise to neutralize risks before they escalate.
Modern fnCyber Security Operations aren't just reactive entities but also predictive and preventive. Constantly updating its threat intelligence database, the center is well-versed in emerging vulnerabilities, zero-day exploits, and Advanced Persistent Threats (APTs). By integrating threat intelligence, leveraging machine learning for pattern recognition, and collaborating globally with other Global Security Operations, these centers remain a step ahead of potential attackers.

The Service Approach
The Drill, aka The Service, starts with evaluating and detailing the historical information, policies, and procedures, reviewing the existing baselines, and understanding the requirements. The vanilla support model falls onto the proven NIST Incident Response Life Cycle with NIST SP 800-61r2, a Platinum Standard in IT Security and Cyber Threat Response at its core. After that, calibrate and enhance the SOC throughput leveraging fnCyber Security Consulting devised Resilience Framework to Evaluate, Engineer, Deploy, and Configure.
Transitioning into the Engineering of the Design, the emphasis shifts to crafting a detailed blueprint of the prospective Security Operations infrastructure. Both hardware and software components are taken into account. During this stage, the focus is also on selecting the apt security tools, ranging from SIEM systems to threat intelligence platforms. A critical component of this phase is discerning and mapping out the integration touchpoints with the central platform to ensure fluid data exchange and system interoperability. As the process moves to the Deployment phase, the design theory takes a tangible form, setting up the Security Operations infrastructure and deploying the previously selected tools, ensuring their alignment with defined security protocols.
Next, the Configuration & Fine Tuning phase takes precedence, intending to tailor the Security Operations to the organization's unique threat landscape by developing specific use-case scenarios and customizing alert thresholds. An essential element of this stage is the configuration of dashboards, which later serve as the nerve center for real-time insights.
The training and knowledge transfer phase emerges as indispensable for ensuring the human element is not overlooked. Through hands-on training sessions, Security Operations personnel are equipped with the skills to navigate the new systems and tools. Simulated cyberattack drills test the prowess, while a continuously updated knowledge base is a guiding light.
fnCyber promotes a Threat Response plan based on the combination of Asset - Risk - Response. Evaluate existing IT Security Controls that offer a level of protection and help lower the overall security risk to the asset so it can fit into a standard incident response plan; alongside monitoring and alerting solution with an automated pre-configured response helps to lower the burden on SOC and straight away engages the SOC analyst to the Post-Incident Recovery. Next is to Engineer a Holistic SOC Capability and Preparedness based on Asset - Risk - Response and Protection Profiles with a fully evolved SOC Knowledge Base.

The Phases
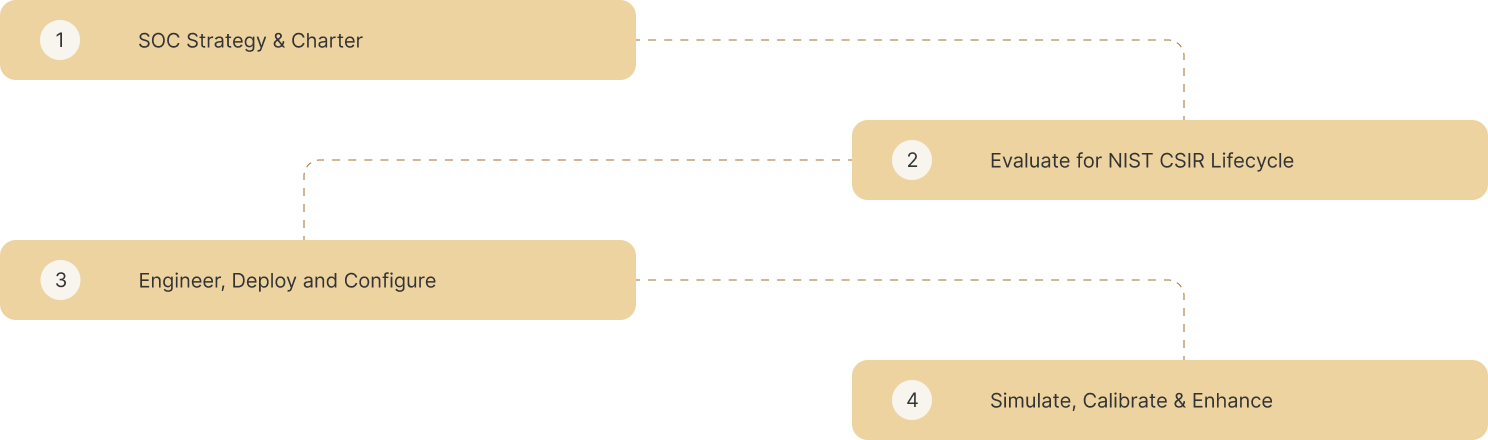

SOC Capability Maturity is enhanced with fnCyber Security Consulting’s undeterred simulation schedules replicating real-life complexities to improve the Operational Success of the SOC Readiness and response; when coupled with a 7-step Improvement Process, eliminates Non-Value Adds to optimize resources, effectively creating a Robust High Performing IT Security Threat Response Capability.
Select & Explore the Security Operations
"fnCyber Security Operations - A SOC-Operating System enhanced with a Cyber Resilience Thought Engine"
Resources

Articles
Security Strategy Intelligence - Practices and more


Case Studies
Realworld Business Challenges - Keep it Targeted and Simple


Archives
Infrastructure Security - What makes it so critical


Contact Us

fnCyber Security Consulting Services Pvt. Ltd., Level 1, Salarpuria Knowledge City, InOrbit Mall Road, HITEC City, Hyderabad, Telangana 500081 India

fnCyber Security Consulting Services B.V., Johan De Wittlan 7, The Hague 2517 JR, Netherlands
+31 6 2999 7281

