Security Design & Blueprinting
Improve Business Operational Resilience with Secure-by-Design Systems and Infrastructure

Security Design & Blueprinting for Business Continuity
In the journals of computing history, security was often an afterthought, added as a reactive measure to incidents and breaches. However, as the digital world evolved and cyber threats became more sophisticated, the reactive approach revealed its inherent flaws. Frequent security breaches, financial losses, and eroded public trust signaled an urgent need for a paradigm shift in how cybersecurity was approached.
Drawing inspiration from architectural and engineering disciplines, where designs and blueprints form the essence of construction, fnCyber Security Consulting began to see parallels in constructing secure digital systems. Recognizing the importance of a well-laid plan before execution, fnCyber Security Consulting adopted similar principles, ensuring every digital structure built had its security foundation firmly in place, hence the Security Design and Blueprinting services.
Ensuring a robust cybersecurity posture remains paramount in the intricate digital transformation landscape. Security Design and Blueprinting emerge as a foundational process, paving the way for robust and resilient IT systems architectures. At the heart of this offering lies a thorough understanding of the threat landscape, complemented by adept use of cybersecurity frameworks, controls, and best practices.
The importance of this proactive approach cannot be overstated. By engaging in meticulous planning and design, organizations can foresee potential vulnerabilities, understand the threat landscape, and plan mitigation strategies before a single line of code is written or a network is set up. This foresight translates to a cost-effective strategy, reducing the expensive repercussions of post-breach remediations.
Moreover, Security Design and Blueprinting align with an organization's broader objectives. Integrating security requirements with business goals from the outset ensures that security doesn’t become a hindrance but rather an enabler of business functions. This holistic approach secures an organization's digital assets and enhances trust with stakeholders, clients, and customers.
Today's digital enterprises are always prone to threats that constantly evolve and adapt; adopting a strategic, well-planned blueprint ensures an organization remains agile. It can respond to new threats, adapt to changing business environments, and safeguard its assets. In essence, Security Design and Blueprinting provide the strategic foresight to navigate the Present and the Future Cyber Landscape.

The Service Approach
Ensuring a robust cybersecurity posture remains paramount in the intricate digital transformation landscape. Security Design and Blueprinting Service emerge as a foundational process, paving the way to provide robust and resilient IT systems architectures. At the heart of this offering lies a thorough understanding of the threat landscape, complemented by adept use of cybersecurity frameworks, controls and best practices.
Initiating a comprehensive threat modeling exercise identifies potential vulnerabilities within systems and processes. Potential threat vectors are examined by leveraging industry-leading methodologies, such as OWASP and STRIDE. Data flow diagrams and architectural patterns also provide a visual representation, providing a holistic view of security touchpoints.
With the blueprinting phase, attention shifts to the creation of strategic roadmaps. Crafted with precision, these roadmaps create repeatable processes and offer a sequential guide to implementing security controls, countermeasures, and protocols. Utilizing principles from frameworks like NIST, ISO 27001, and CIS, a balanced mix of preventative, detective, and responsive measures are integrated. Encryption strategies, Intrusion Detection Systems (IDS), and Security Information and Event Management (SIEM) tools find their rightful place within this blueprint. A dedicated focus on physical and virtual environments ensures comprehensive coverage. Virtualization security, network segmentation, and secure coding practices harmonize to form a well-rounded security design. Security Design and Blueprinting is not just a service; it's a strategic approach to cultivating a cyber-resilient environment where business continuity and data protection are at the forefront of every architectural decision.

The Phases
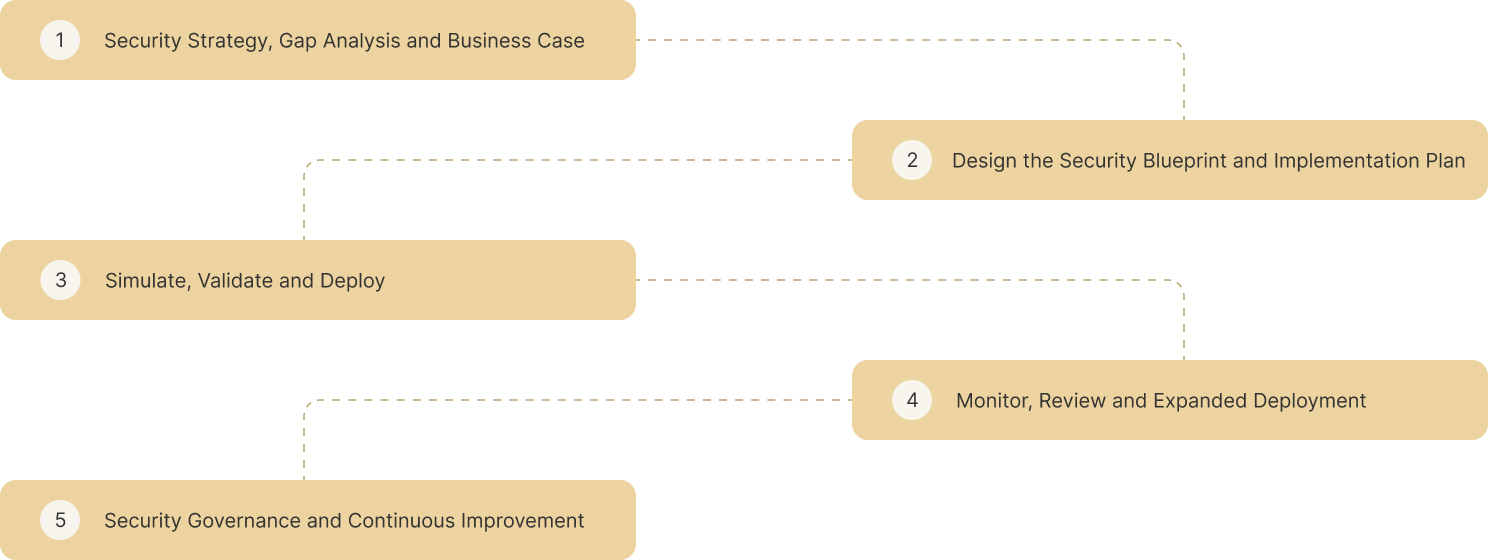

In the competitive digital marketplace, where robust cybersecurity practices differentiate leaders from the rest, Security Design and Blueprinting emerge as a quintessential business imperative. Integrating prescient planning with cybersecurity paradigms offers organizations a competitive edge—enabling them to safeguard critical assets while optimizing operational efficiency. As global cyber challenges intensify, the strategic alignment achieved through this methodology ensures both resilience and continuity. Thus, ensuring meticulous cybersecurity design and a well-articulated blueprint is non-negotiable for businesses aiming to maintain market leadership.
Select & Explore the Security Design & Blueprinting
"Incorporate Security Design and Blueprinting as an Investment to create Sustainable Business Resilience"
Resources

Articles
Security Strategy Intelligence - Practices and more


Case Studies
Realworld Business Challenges - Keep it Targeted and Simple


Archives
Infrastructure Security - What makes it so critical


Contact Us

fnCyber Security Consulting Services Pvt. Ltd., Level 1, Salarpuria Knowledge City, InOrbit Mall Road, HITEC City, Hyderabad, Telangana 500081 India

fnCyber Security Consulting Services B.V., 6th Floor, HSD Campus Wilhelmina van Pruisenweg 104 2595 AN Den Haag
+31(0)70 2045180

