Security Audits
Leave No Security loopholes in the Enterprise Infrastructure

Security Audits serves as a Health Check
In the contemporary digital epoch, the internet, the web of cyber networks has become the foundation upon which organizations construct their operations and ambitions. While acting as a catalyst for unparalleled growth and global connectivity, this vast digital tapestry also unveils a complex maze of potential vulnerabilities. Each node and junction in this web might offer points of exploitation for cyber adversaries, who are continuously evolving and seeking new avenues to infiltrate.
These digital loopholes, intentional or unintentional, can jeopardize not just data but also the essence of an organization's reputation and trustworthiness. It's a dynamic battleground where the stakes are high—every byte of data, every transaction, and every user interaction can become a potential frontline. Cybersecurity Audits recognize the intricacies and gravity of these looming threats as the very first step. The quintessential challenge lies in preempting these vulnerabilities, understanding their myriad forms, and building robust fortifications against the onslaughts that the digital realm is invariably subjected to.
Enter the realm of the Cybersecurity Audit — a rigorous, structured examination of an organization's digital safeguards. Security Audit is a snapshot of an entity's cyber health and a profound dive into its digital processes, tools, and protocols. These audits are comprehensive to evaluate the robustness of firewalls till scrutinizing the rigor of passwords and protocols further.
Navigating the intricate corridors of the cyber realm requires more than mere technical prowess — it demands an intuitive understanding of the ever-evolving digital threat landscape. fnCyber Security Consulting is a beacon in this vast cyber world, renowned for its expertise, resilience, and commitment to safeguarding digital infrastructure.

The Service Approach
Navigating intricate cyber corridors demands more than technical prowess—it calls for an intuitive grasp of an ever-evolving digital threatscape. At the intersection of expertise and resilience in this vast cyber domain stands fnCyber Security Consulting. Cybersecurity Audits, more than just a service, embodies a distinct creed. In-depth expertise at its foundation; each cybersecurity audit is approached with unmatched analysis and dedication. Recognizing the unique digital fingerprint of every organization, tailored strategies form the cornerstone of audit processes, ensuring meticulous and resonant assessments.
Surface-level evaluations merely scratch the surface. Multilayered analytical approaches delve deep, spotlighting both overt and covert vulnerabilities. Such meticulous exploration, spanning from overarching infrastructure to individual IT Components, offers unparalleled insights into potential breach points. In the shifting landscape of cyber threats, static defenses prove inadequate. Adaptive methodologies ensure that audit processes and strategies evolve coherently with emerging threats. fnCyber prides itself on its adaptive methodologies, ensuring that the audit processes and strategies evolve coherently with the dynamics of emerging threats.
fnCyber values collaborative engagement and views each service as the beginning of a partnership, extending the commitment beyond the audits. Organizations benefit from actionable insights, continuous training modules, and unwavering support, laying the foundation for long-term cyber resilience. With such a multifaceted approach, fnCyber doesn't merely identify vulnerabilities but helps lay the foundation for digital resilience.

The Phases
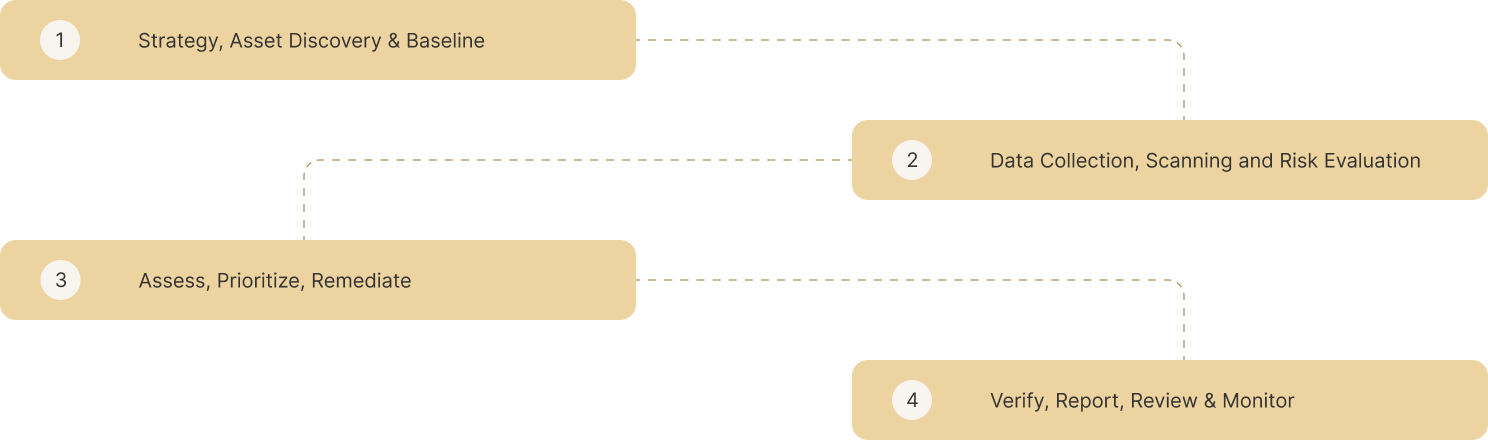

fnCyber Security Consulting has learned from The Center for Internet Security [CIS] with a prescription of 20 tried and tested defensive controls that have been proven across Industries, 5 of which can effectively prevent 80% of the attacks, and organizations will transform to become super resilient if all 20 are adopted.
Select & Explore the Security Audits
"Build Cyber Resilient organizations with a combination of Cybersecurity and IT Services Best Practices."
Resources

Articles
Security Strategy Intelligence - Practices and more


Case Studies
Realworld Business Challenges - Keep it Targeted and Simple


Archives
Infrastructure Security - What makes it so critical


Contact Us

fnCyber Security Consulting Services Pvt. Ltd., Level 1, Salarpuria Knowledge City, InOrbit Mall Road, HITEC City, Hyderabad, Telangana 500081 India

fnCyber Security Consulting Services B.V., 6th Floor, HSD Campus Wilhelmina van Pruisenweg 104 2595 AN Den Haag
+31(0)70 2045180

