Understand Common Attack Patterns
Understand Common Attack Patterns

CAPEC - Common Attack Patterns Enumeration and Classification
What is CAPEC?
MITRE CAPEC is a comprehensive dictionary of known attack patterns adversaries exploit weaknesses in software applications, hardware appliances, and IoT devices. The US Department of Homeland Security initially released it in 2007 to improve software assurance through security awareness at the development stage. It now serves security analysts, software and hardware developers, testers, and educators to build more robust cyber-security resilient products. The current version as of 2021 is version 3.6, which has 546 attack patterns [1]. CAPEC attack patterns are classified into 6 "Domains" and 9 "Mechanisms" of Attack.
Domains of Attack:
- Software
- Hardware
- Communication
- Supply Chain
- Social Engineering
- Physical Security
Mechanisms of Attack:
- Engage in Deceptive Interactions
- Abuse Existing Functionality
- Manipulate Data Structures
- Manipulate System Resources
- Inject Unexpected Items
- Employ Probabilistic Techniques
- Manipulate Timing and State
- Collect and Analyze Information
- Subvert Access Control
The information in a CAPEC profile is extensive. For example, CAPECs include an ID for tracking and correlation, attack name, high-level description, attack execution procedure, attack prerequisites, severity scope and score, attacker skill requirements, attack success rates, and mapping to CWE (Common Weakness Enumeration).
Extending CAPEC
Mapping to CWE dramatically expands the capabilities of CAPEC because CWE can be correlated from a CVE product vulnerability back to a high-level attack pattern. The traversal between high-level attack information and specific product vulnerabilities enhances threat intelligence and mitigation efforts. An extensive MIT white paper provides a detailed description of stitching CAPECs to MITRE ATT&CK and CWE, CVE, CVSS, and CPE data [2]. Figure 1 visualizes how CAPEC's extension extends from high to low-level information.
For example, let us look at CVE-2020-16875 found in 2020 [3]. The NIST enriched CVE details include the "Weakness Enumeration" field denoting the related CWE category and other valuable information such as vendor advisories and remediation information, CVSS (Common Vulnerability Scoring System), and CPE (Common Platform Enumeration) mapping the vulnerability to a specific product(s). In this case, the CVE represents a severity score of 7.2 and affects Microsoft Exchange Server software versions between 2013 and 2019 with cumulative updates. The CWE categories listed are CWE-74 Improper Neutralization of Special Elements in Output Used by a Downstream Component and CWE-269 Improper Privilege Management. In addition, following CWE to CAPEC reveals several categories related to improper input handling and CAPEC-233: Privilege Escalation. Complete CAPEC, CWE, and CVE data are publicly available from MITRE [7][8][9], and the extended CVE to CWE and CPE is available from NIST [10][11].
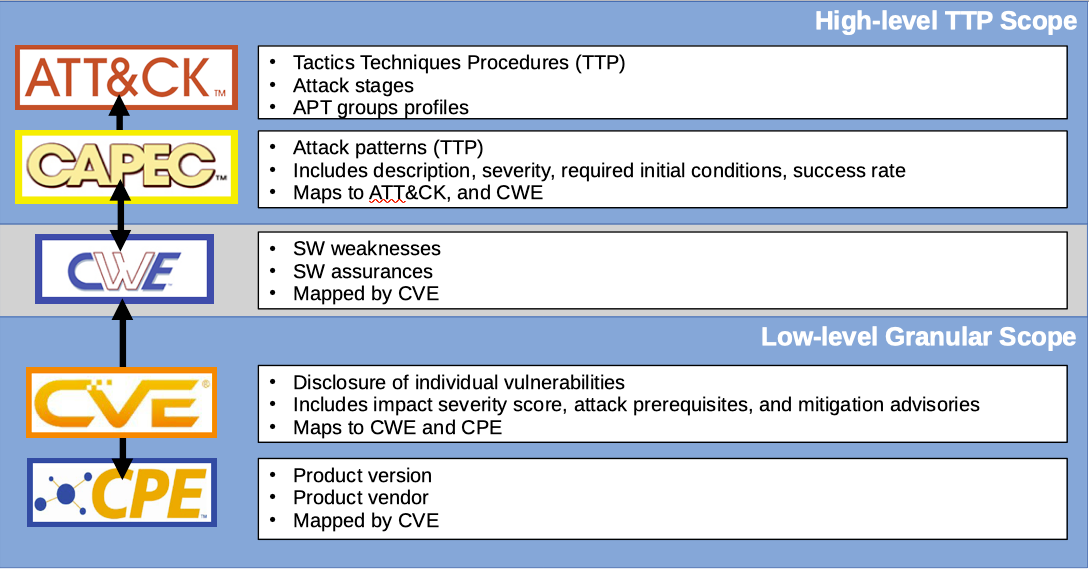
Figure 1. Schematic shows data mapping from high-level TTP to low-level granular information to enhance threat intelligence.
How Does CAPEC Correlate to ATT&CK?
MITRE ATT&CK connects the various tactics of a cyber attack campaign with particular techniques and procedures (TPP). The framework allows insight into cyber attack elements chaining to achieve a malicious end goal.
Like ATT&ACK, CAPEC approaches attack patterns from a Tactics, Techniques, and Procedures (TTP) perspective. However, 112 out of 546 total CAPECs have been mapped directly to ATT&CK tactics and techniques via the "Relevant to the ATT&CK taxonomy mapping" field available on relevant CAPECs [4] 244 courses listed in ATT&CK. Therefore using ATT&CK and CAPEC is required for a comprehensive security perspective.
This mapping bridges the adversarial perspective (external) and the security perspective (internal). When starting from the ATT&CK tactic, mapping ATT&CK to CAPECs enables connecting attacker strategy to existing products through CWE to CVE and CPE specifics and a category of software development vulnerability through CWE classifications.
"CAPEC" Use Cases
MITRE has also provided eight main and twenty-six sub-categories of known use cases [5]. These apply to software development, security architecture, compliance, training, and policymaking, and US Homeland Security has advised the application of CAPEC to security-focused software development [6]. Below is a summary of those use-cases:
- Application testing
- Threat Analysis for Mitigation, Auditing, and Compliance
- Threat Modelling
- Policy Requirements
- Evaluations
- Reporting, Advisories, and Alerts
- Training / Education
- Prioritization of Vulnerability Management Items
New software vulnerabilities are disclosed via CVE every day. Patching CVEs is a reactive approach. However, a bullet-proof cyber-defense needs to be proactive. CAPEC provides the Threat Intelligence required for detection and response for security engineering and orchestration addition; In addition, CAPEC attack patterns can be used to build high-level threat perspectives and correlating CAPEC, CWE, CVE, and CPE data enable traversal between high-level information such as attack patterns and low-level information such as affected products with known information vulnerabilities or vice versa.
Finally, CAPEC includes attack patterns mapped to a CWE classification wherever they are not mapped to a CVE, indicating that some CAPEC attack patterns can only be mitigated through policy or software configurations as they do not represent a vulnerability in software code but rather a weak implementation or configuration.
Conclusion
CAPEC in itself includes a wealth of vulnerability information relevant to software, IoT, and hardware development, providing those managing development teams with a toolkit for setting policies and designing software architecture that provides a higher degree of assurance. Extending CAPEC with associated threat intelligence and vulnerability data available from MITRE and NIST allows traversal from a high-level to low-level Threat Intelligence perspective. Focusing on development best practices should not be an afterthought when the software and hardware development cycles are fast and furious. Responsibility to end-users is something that software engineers should take seriously, and CAPEC is a good starting point for building software assurances.
References
[1] MITRE - CAPEC Common Attack Pattern Enumeration and Classification
https://capec.mitre.org/
[2] MIT - Linking Threats Tactics, Techniques and Patterns with Defensive Weaknesses, Vulnerabilities and Affected Platform Configurations for Cyber Hunting
https://arxiv.org/pdf/2010.00533.pdf
[3] NIST - NVD National Vulnerability Database (CVE-2020-16875)
https://nvd.nist.gov/vuln/detail/CVE-2020-16875
[4] MITRE - CAPEC VIEW: ATT&CK Related Patterns
https://capec.mitre.org/data/definitions/658.html
[5] MITRE - CAPEC Use Cases
https://capec.mitre.org/about/use_cases.html
[6] US Homeland Security - Understanding How They Attack Your Weaknesses: CAPEC
https://owasp.org/www-pdf-archive//Understanding_How_They_Attack_Your_Weaknesses-CAPEC_-_OWASP_AppSec_DC_2010_(Barnum).pdf
[7] MITRE - CAPEC List Version 3.6 Downloads
https://capec.mitre.org/data/downloads.html
[8] MITRE - Common Weakness Enumeration Data Downloads
http://cwe.mitre.org/index.html
https://cwe.mitre.org/data/downloads.html
[9] MITRE - Download CVE List
https://cve.mitre.org/data/downloads/index.html
[10] NIST - NVD National Vulnerability Database Data Feeds
https://nvd.nist.gov/vuln/data-feeds
[11] NIST - Official Common Platform Enumeration (CPE) Dictionary
https://nvd.nist.gov/products/cpe