fnC - 101 Series - Threat Response Engineering
fnC - 101 Series - Threat Response Engineering

Threat Response is - “What Would you Do” when you know" You are going to get "Hit by Car on a Busy Day rush to Work"
There is a greater risk and threat to privacy and online security in this digital era, where everyone is connected. Cybersecurity is a global concern, and people from all backgrounds need to understand this. You must stay anonymous on the internet to protect your privacy and personal resources. The same applies to enterprises as well. They need to adopt better security solutions, advanced tools, and technology along with an experienced team of security professionals to efficiently prevent attacks, mitigate threats and implement compliance policies and cybersecurity frameworks. In addition, enterprises must develop plans to mitigate vulnerabilities and respond to threats by actively implementing threat response strategies to defend the critical IT infrastructure and other resources against cyber threats.
What is a cyber threat?
A cybersecurity threat aims to steal, damage, disrupt, or stop any system, program, or service by exploiting the active vulnerability present in that very resource.
According to NIST, a cyber threat at any given time, an event or action with the potential ability to impact an enterprises operations and resources via unauthorized information system access resulting in damage to reputation, financial loss, disclosure of confidential data, and information.
Common Cybersecurity Threats
There are various cyber threats, each having a unique structure and motive. Below are the few most common cyber threats.
Ransomware
Ransom is described as extorting money from people/ organizations for freeing something or someone who was kept captive until the amount of consideration is paid for that captivity. In terms of cybersecurity, Ransomware is a type of malicious software specially designed to attack PCs and programs by blocking access privileges and encrypting the data, files, and folders of a user until a ransom amount is paid to the attacker. Even after paying the ransom, it’s not guaranteed that you will get back your files; the hacker may demand more or may never release your resources.
DDOS Attacks
As the name suggests, a denial of service attacks, the smoothly running system services, and resources suddenly stop working and respond when this attack is launched on a target computer. All an attacker needs to do is, overwhelm a system or resource with a vast number of requests so that other recommendations made by legitimate users could not be processed or responded to by that system currently. Attackers use this method of attack to cause harm to the system and to stop the system from running temporarily. When the same attack is launched from too many other affected or hostile systems known as botnets are called Distributed Denial of Service Attacks.
Malware
Malware is a malicious software specifically designed to get unauthorized access or damage a computer system’s files and contents. It is also responsible for making computer systems behave inadequately and may reduce the performance and function parameters. Malware has a huge family and a rich set of siblings. Some are computer viruses, worms, Trojan horses, spyware, adware, scareware, rogue software, and Ransomware.
Phishing
Yes, you’re thinking the right way; it’s pretty similar to the term and practice we use in the real world to catch fish by offering them food and making them fall into our planned trap. Phishing is something like that; you receive an e-mail with an attachment or hyperlinks, actually a trap or fraudulent mail that will seem legitimate from a trusted source like your loved ones or from the bank in which you might have an account. Asking for urgent requests, changing your password, to provide sensitive data and personal information and hence used to gain access to victims account, personal info, resulting in data theft and financial losses.
SQL Injection
An SQL Injection attack is executed as a standard SQL query to the database via the input data from the client to the server. An attacker can launch a SQL Injection attack by simply submitting a malicious code into a vulnerable website search box.
Zero-day Attack
The Zero-Day Attack targets the unknown vulnerability in the system and networks about the user or developer has no idea at all. For example, suppose you downloaded a Cisco application or software and started running it on your system; unfortunately, there’s an unknown vulnerability that you or Cisco doesn’t know of or haven’t discovered yet, but somehow, a bad actor has already discovered that bug or vulnerability. Before Cisco could release a patch file or an update for that unknown vulnerability, the bad actor takes advantage of that time gap and attacks your system. A zero-day flaw is an important aspect or component when designing an application to be secure and efficient.
Man in the middle attack
This attack works when a bad actor inserts some data or themselves in between a two-way communication or transaction. For example, suppose Peter wants to connect to Bob and send a message; before it arrives at Bob, a bad actor intercepts the request, modifies the message body, and then sends it to Bob. This way, Bob wouldn’t know that the message has been altered and would trust that the message has arrived from a legitimate source Peter, at the other end, when Bob sends some message to Peter, again the bad actor can modify the contents of that message before sending it to Peter. This way, both Peter and Bob trust each other by not knowing there’s a man in the middle watching and altering the content and data in transit.
How to identify Cyber Threats?
Cyber threats are critical and sophisticated to the entire digital network system across the globe. To build a reliable and secure network and workforce infrastructure, identifying these threats has become a crucial exercise for organizations. Threat identification becomes relevant when you know about the threat landscape, latest trends and, sector-related resources. Threat identification also depends on the capabilities and skills of the in-house tools, technologies, and security professionals. Further, having internal vulnerability management and assessment programs helps enterprises identify the evolving and zero-day threats in no time. Organizations with critical IT infrastructure need to keep their eyes open on threat landscape reports and facts.
How to prevent Cyber Threats?
Prevention is better than cure. This can be correlated with preventing cyber threats rather than looking for workarounds after a successful cyber attack. Preventing cyber threats involves various elements and steps. One is to have a better IT compliance policy and cybersecurity frameworks developed by NIST and ISO
There are various international cybersecurity compliance standards and frameworks to follow and implement. Organizations can have any of these implemented in their infrastructure. Since open-source and government organizations develop these frameworks to help fight cyber-crime and tackle global cybersecurity concerns.
The best possible way to prevent cyber threats is to remediate them once they are detected. A good start will be training and educating the workforce to adopt proper security measures and essential security patch management. If the Non-IT professionals are well aware of the threats, they can play a severe role in preventing cyber threats, even being the weakest links in an enterprise. Vulnerability assessment and management programs further bring insights and transparency to the current state of networks, systems, and the overall IT environment of an organization. The larger the scope and infrastructure grow - the higher the demand for advanced threat identification and detection solutions becomes necessary.
The Threat Landscape
Since the Covid-19 pandemic, the cybersecurity industry has seen a significant rise and expansion of the cyber threat landscape. With Ransomware leading from the front, phishing and malware threats are just behind it.
A quarterly report on evolving cyber threat landscape 2021 Q3 from Zerofox highlights how various threats are evolving significantly.
Another threat landscape study report from Helpnetsecurity claims social engineering as the top and concerning issue for the global cybersecurity market.
Data breaches are increasing enormously, and enterprises need to take them seriously now. The statistics on the data breach report for 2021 published by Verizon are horrifying for all organizations.
According to Verizon-DBIR Data Breach Investigation Report 2021; Social engineering, denial of service, and Ransomware are the top three threats and reasons for data breaches.
Another statistic states that 85% of data breaches occurred due to the involvement of the human element, 36% were the result of Phishing, and 10% were due to Ransomware.
What is Threat Modeling?
According to Global Tech Council, threat modeling is a process of identifying, detecting, analyzing, and addressing potential vulnerabilities or threats that cybercriminals can use to gain unauthorized access to an organization’s private network resources and infrastructure. Cybercriminals can capitalize on the momentum of unauthorized access by exploiting the active vulnerabilities and threats. This results in intellectual property and reputation damage, service disruption, and inconvenience in business continuity. The threat modeling process involves identifying valuable and critical assets enterprises want to protect, prioritizing them based on vulnerability severity, and implementing appropriate countermeasures to mitigate them. The threat modeling process generates an abstraction of the potential threat and adversary.
The threat Modeling Process
There are various ways to implement the threat modeling process to secure their infrastructure from cyber threats. We will discuss below a standard practice used by enterprises.
Critical Assets Identification: Before implementing or recognizing potential vulnerabilities across your IT ecosystem, it is essential to understand or have an idea of the valuable assets and resources you’re trying to protect. Why is this step crucial? Because enterprises need to prioritize their assets.
For instance, let’s say their ERP system is an integral part of their daily business, and any weakness or vulnerability on any level can not be accepted. So the ERP system would be a top priority and choice among other resources for vulnerability or risk assessment.
Whether a process, service, or a physical component inside the ecosystem, must be identified that could be targeted. Covid-19 pandemic forced the world towards digital transformation, making the asset identification more complex and challenging to analyze.
Potential Threat Identification: When done with the asset identification phase, the threat identification jumps in. To effectively identify threats, vulnerabilities need to be discovered across the ecosystem. This way, enterprises get an outlook on the potential vulnerabilities that could be exploited. Vulnerabilities and threats are two different things yet connected and dependent on each other. Vulnerabilities can be identified using numerous mechanisms. You can contact your service provider or vendor to get intel about the presence of active vulnerabilities and potential threat factors causing high risk in their device or services. Organizations can also check the open-source threat intelligence platforms for the latest vulnerability and threat trends. One good place to start inspecting the top web application vulnerabilities in 2021 is OWASP. Once potential threats are identified, it becomes a piece of cake for security professionals to enforce countermeasures and mitigate them. Threat identification is relatively helpful and makes other stuff easier for the blue team.
Threat Mitigation or Designing Appropriate Countermeasure: All the discovered vulnerabilities and identifying threats that could exploit them prepare organizations to adopt extreme defense methodology and solutions. This phase in threat modeling prepares organizations for a better threat defense strategy. Threat countermeasure strategy designed with the help of experts and security team assists enterprises on threat remediation suggestions.
Validate: This phase validates whether the previous processes have been implemented correctly or not. The threat modeling validation phase also ensures organizations have acted on the earlier stages. What solution has been implemented and helps prepare the data model for future references.
Threat Modeling Methodologies
The Global Tech Council recognizes the following as top threat modeling methodologies
- OCTAVE – Operationally Critical Threat, Asset, and Vulnerability Evaluation - Focused on assessing organizational (non-technical) risks that may result from breached information assets.
- PASTA: risk-focused approach: Process for Attack Simulation and Threat Analysis

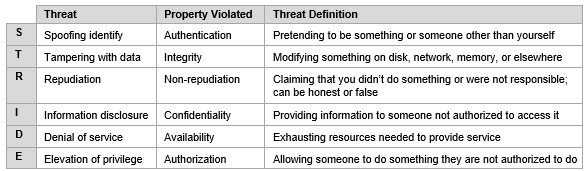
- STRIDE (Uses application-centric approach)
- TRIKE – Risk-based approach with the risk-modeling process and unique implementation using CRUD - (Creating, Reading, Updating and Deleting)
- VAST – Visual, Agile, and Simple Threat Modeling
Some of the other best threat modeling methodologies used in the cybersecurity industry are
Microsoft Threat Modeling Tool
What is Incident[Threat] Response?
Incident response is a structured process that prepares enterprises for response strategy in a security breach. It is an organization’s systematic approach to an attempted data breach or a cyber attack. Cyber-attack and data breaches can cripple an organization’s active service and operations, resulting in data loss, reputation damage, financial losses, intellectual property, assets, brand value, and other resources as well. An advanced incident response plan or strategy can dramatically limit and reduce the attack damages and lower the security team’s costs and effort. The incident response process aims to identify, contain and reduce the attack possibilities and help organizations recover quickly from the damages.
A research study done by a Cyber Resilient Agency shows that 77% of businesses lack an advanced or consistent incident response plan
The Incident/Threat Response phases.
NIST Cybersecurity Framework has categorized the incident response lifecycle into the following phases.
Preparation: Preparation is the most critical phase in the incident response plan as it determines how an organization will respond to threats insurgence of an attack. The preparation phase begins with policy creation, response strategy planning, talent and tool selection, and security team formation. The Preparation ensures that everything has been adequately planned and executed accordingly when an actual attack occurs.
Identification & Detection: The identification phase deals with incident identification and detection. It determines if an incident has occurred or not; it does so by collecting logs and messages from IDS, Traps (Anti-Virus), Firewalls, early warning systems, and threat monitoring solutions as well. The primary function of this phase is to identify the threats and real-time incidents based on the collective security events, error messages, and logs generated by various networking and security appliances. If an incident or an attack has occurred, it should be immediately reported to the concerned team or department. When the incident is reported to the CSIRT (Computer Security Incident Response Team), it allows them to prepare for further actions and countermeasures to be implemented proactively.
Containment & Eradication: Once the attack instance and its type have been identified and detected, the Containment & Eradication phase comes into action. Containment limits the further damages posing a high threat by the detected incident or attack. It limits additional damages by response plan designed in the preparation phase, including endpoint isolation, traffic route change, shutting down the affected host/server, and bringing up the redundant backup peer. Containment also gathers collective and real-time shreds of evidence to perform deep analysis and inspection. The collected evidence can be further used for future legal proceedings and prevent similar attacks. Eradication deals with the removal and refinement of affected systems and resources. This phase ensures corporations that earlier infected hosts or services have been inspected and cleaned thoroughly and can be used back in the production environment. Eradication prevents the risk of reinfection and protects the organization’s resources from getting compromised again.
Recovery: The recovery phase is responsible for bringing the affected systems back into operation. This can be implemented either by administrators, CSIRT, or the security team. Recovery from infections and attack instances may include restoring from clean backup files, new software versions, installing patches, building systems from scratch, and the list goes on. This phase also insists on verifying if the restored systems are cleaned up and can’t be reinfected if the systems are mitigated against the infection or attack and are fully operational as before.
Lessons Learned: This is one of the most critical phases in the incident response lifecycle to which every security team shall pay attention. Learning and improving is part of evolution, and every day, there’s something new to learn. The incident response team should proactively reflect on evolving threats, improved tools, and advanced technology. They should conduct special sessions post-attack incidents to share evidence and discuss lessons learned from the recent incident. Once again, the incident response plan needs to have complied with additional details and evidence originating from the recent attack to benefit future incident response. The incident response team should ask each other the following;
- How was the issue detected, when, and by whom?
- What time did the incident take place?
- Root cause analysis of the incident
- How was the incident contained and eradicated?
- What information was needed?
- Sectors where the CSIRT got effective and areas for improvement
- How the information sharing with other enterprises have been improved?
- Corrective actions and steps that can prevent similar incidents in the future?
- Additional tools and technology required to detect, analyze, and mitigate future incidents?
Conclusion
With the ever-evolving threat landscape and rapid digital transformatioit’st’s high time to secure your organization from the latest cybersecurity threats and data breaches. Traditional security solutions like firewall and anti-virus solutions alone can only help some extenToday’sy’s sensitive and critical IT ecosystem needs threat intelligence and AI-powered machine learning security solutions to proactively identify, detect, mitigate and recover from cybersecurity threats and attacks.
Top Cybersecurity threat infographics to look for:
Fortinet Global Threat Response Landscape
Accenture Cyber Threat Intelligence Report 2021
ZeroFOX Threat (Ransomware) Landscape Report 2021